Breaking a steganography software (without even downloading it) :
Steganography 1.50 and 1.60
|
Steganography strength (is it easy to see there is hidden data?): Low Cryptography strength (is it easy to recover the hidden data?): Low |
|
A company called Pipisoft (which is a very funny name from a french-speaking perspective, because it means "peesoft") sells a steganography software called Steganography for 25 US$. This software seems to be part of a suite of security sharewares called SecureKit. I didn't have to download, install or execute this software to crack its steganography scheme. One week after I sent them an email to tell them about the page I wrote about the version 1.50 of their software, they suddenly updated to a new version 1.60. Great. These are reactive programmers. And that's one of the reasons I present these results: so people can increase the security level of their products. Unfortunately, the new version is as weak as the precedent one. The concept is exactly the same. I've written a new paragraph about it, see below. If you want to understand how this program works, you still have to read the first paragraph. 1. Steganography version 1.501.1. How does it work?They actually offer an online demo with an example of a JPG image carrier ("result.jpg") hiding another JPG image inside. So I just downloaded this demo image, and opened it with an hexadecimal editor. Than I searched for the EOI (End Of Image) marker of the JPEG format, which is supposed to be at the end of the image data stream: two bytes "FF D9". It was not at the end, a clear sign that something was fused after the normal end of the image. Around the EOI, I saw this:
In white, the end of the JPG carrier image, with the EOI marker underlined. In yellow, "hidden" bytes. No need to check further. The "PK" marker said everything. We understand how it works. The "hidden" JPG file (called "jennifer.jpg") is actually compressed in a ZIP file, and concatenated at the end of the image carrier. That's probably why they say in their website that this software uses "advanced compression" (which is indeed true). Same strategy than the precedent software I analyzed, SQFileHide. And same level of security: the hidden data is *very* visible. 1.2. More funI finally downloaded and installed an evaluation copy of the software, because I wanted to check this claim on the website "It uses 256 bits encryption". I was curious about which algorithm they were using. Blowfish? AES? TwoFish? TripleDES? They actually don't use any encryption. They probably think they do, but the fact is that the hidden data is not encrypted and can be extracted without any particular tool, even when you set a password. Here are three examples of a text file called "hiddenmessage.txt" added after a small JPG of mine. We now know that it will be included in a compressed ZIP file and concatenated at the end of the carrier. Here is first the file added without password, as seen on a typical hexadecimal editor. The offset is on the extreme left (this is the position of the bytes in the file), the hexadecimal bytes are in the middle (the value of each byte, shown in hexadecimal form), and the ASCII translation of these bytes are on the right (how these bytes would look when seen with a text editor). The end of the JPG file is in white, with the End Of Image marker underlined. The "hidden" text, in a perfectly valid ZIP container, is in yellow. You can see the "PK" markers and the name of the file inside the ZIP. Then there are a few bytes added by the steganography program, starting with a "HIZ" marker, in red. I've underlined a funny looking string of 16 bytes in this red section.
Here is the file added with password "a". You can see that the hidden data, in yellow, is exactly the same. Which means that there is no encryption. The red underlined part is actually the only one that changes when you add a password.
Here is the file added with password "b". Once again, nothing changes, except the red underlined part.
So why this red underlined part, the only one that changes when you set up a password, is funny looking? When your eyes are used to look at hexadecimal data, you can see that the ASCII translation of these bytes (on the right) looks like hexadecimal values (number from 0 to 9, and letters from A to F). In other words, it looks like these bytes are stored in a strange format, which actually takes twice the space, because one byte is stored as 2 bytes (for example, a byte value of 255, which is "FF" in hexadecimal, would be stored as the 2 bytes "102 102" or "66 66" in hexa, which is the ASCII representation of "FF"). Weird. Anyway. My guess was these bytes would be some kind of hash of the password. I was right. You can check with some free utility like HashCalc that it's actually a MD5 hash: 128 bits (16 bytes) MD5 hash of string "" is " 128 bits (16 bytes) MD5 hash of string "a" is " 128 bits (16 bytes) MD5 hash of string "b" is " You can compare with the red underlined values above. Another surprise is that the programmers of this steganography software take some freedom with the MD5 hash: they just store half of the MD5 bytes! That's probably the weirdest thing in this already strange software. La cerise sur le gateau, as we say in France. And it's the demonstration number 783265832 (and counting) that if you use secure algorithms in a wrong way, you don't add any security. Here we have the typical demonstration: MD5 hash is a secure enough cryptographic algorithm, but the way it is implemented in this software is completely and totally and absolutely useless. 1.3. So how do you extract "hidden" and "encrypted" data?Two possibilities: - calculate the MD5 hash of the password of your choice and overwrite the current password hash bytes (at the red underlined position in the exemple above). Then you can extract the data with Steganography 1.50 software. - don't bother and just copy-paste the ZIP file bytes (the yellow ones in the exemple above), and open the file with Winzip. 2. Steganography version 1.602.1. What's the difference with the precedent version?Conceptually, there is no difference at all. They just added a quick obfuscation layer to hide the obvious use of a ZIP file format, and to outdate my precedent analysis. So the hexadecimal dumps in the precedent paragraph cannot be read literally anymore, and we cannot anymore copy/paste the "hidden" bytes and read them directly with Winzip. But strip out this small layer, and it's still the same. A quick obscurity trick does not enhance the security level. Let's have a look.2.2. Show me a new hexa dump!Here is a new small text hidden at the end of another JPG, using the password "a". Color coding is the same than above. We can see that the ZIP file is now somehow encrypted. No structure is visible. But the final red data starting with "HIZ" is still here. And the 16 funny looking bytes are still here too, although a little bit different.
For some reason I'm not showing here, I suspect the obfuscation of the ZIP file is very weak. But it's not really worth spending the minutes to break it. Why? Because you don't need it to recover the "hidden" data. Let's look more into the 16 red underlined bytes. We remember that in version 1.50 of this software, it was half of the MD5 of the password. For password "a", we had: v1.50: 30 63 63 31 37 35 62 39 63 30 66 31 62 36 61 38 0cc175b9c0f1b6a8 And now, with the same password "a", we have: v1.60: 38 6B 6B 39 3F 3D 6A 31 6B 38 6E 39 6A 3E 69 30 8kk9?=j1k8n9j>i0 When there was no password, the bytes were, with v1.50: v1.50: 64 34 31 64 38 63 64 39 38 66 30 30 62 32 30 34 d41d8cd98f00b204 And now, with the version 1.60, we have: v1.60: 6C 3C 39 6C 30 6B 6C 31 30 6E 38 38 6A 3A 38 3C l<9l0kl10n88j:8< So it looks like they obfuscate this data by just adding 8 to every byte. Wow. Powerful encryption method. Don't forget that this field is what the program uses to verify the password you enter is correct. The hidden data itself is not encrypted depending on the password. So now we can use whatever password we want to fool the program, or just remove it. So the first method to extract the data is still valid. Calculate the MD5 of your favorite password, just get the first half, add 8 to each byte of the ASCII representation of the hexadecimal value, and overwrite them in the HIZ structure at the end of the camouflaged file. Or, simpler, just write the bytes 6C3C396C306B6C31306E38386A3A383C into this field and you can extract any data you want without entering a password. 2.2. Temporary files typical errorJust a note about another security hole in this program. Well, I'm not sure it can be called a hole, as the program has no security at all already. A lot of programs use temporary files while they are working. They calculate something, and to avoid using memory, or for some reason it's more convenient, they create a new file on the hard drive and write some content in it. Then, after some time, they delete it and go ahead with their tasks. Serious encryption programs generally avoid to do that, especially writing temporary files with passwords or data before encryption, because it can be a security hole. You know that deleted files are not really deleted. They disappear from the directory list, but their content is still here on the hard drive, and depending on the amount of free space you have, it may stay there for a while. So you think that your porn files are safely encrypted and hidden, but actually, because of this security hole, they are all around your hard drive, very easy to find with any kind of undelete program or hard disk sector viewer. The good security programs, when they really have to write temporary files, after using them, wipe their temporary files by overwriting them several times with some kind of pattern, so the old data totally disappears from the magnetic support. The bad security programs copy and spread your secret data all over the hard drive in temporary files, and attackers can read and enjoy them whenever they want. That's what is happening with Steganography. You can check it easily by looking in the windows\temp folder while you are using this program. Here is what you have in this folder when you hide a file, just before you save the final file: 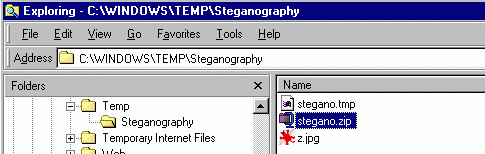 These are 1. a temporary file which is the obfuscated ZIP, 2. the ZIP file which contains your secret data before it's fused at the end of the image, and 3. the image carrier. Here is what you have when you unhide a file: 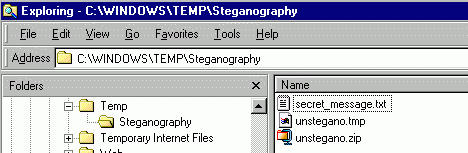 In both case, unknown to you, your secret data is duplicated all over the place, in a zip or in plain form. When the program delete these files, their content is still here. Someone using the computer after you can get it easily by using some kind of undelete program. 3. The conclusionThe conclusion is simple. It's actually a a question I'm asking myself. I don't know anything about cooking, so I'm not going to publish recipe books. I don't know anything about astrophysics, so I'm not going to publish a scientific paper about black holes. So why people who obviously have no idea about computer security suddenly decide to write security software? I thought that the only interesting thing in this software was its nice graphical interface. But after all, it's not that original: Screenshot of their interface:  Screenshot of the website GUIStuff:  Have a nice day! Guillermito, January 24th 2004 |